April 29, 2024
Data Labels and DLP:
- Data labels within DLP (Data Loss Prevention) Policies are configured to include label-based conditions (for example, Confidential or PII) that trigger specific actions which enhance an organization's data protection, promote regulation compliance, and reduce the risk of data leakage or unauthorized access.
- Where there is no integration of data labels with DLP, the data is still classified with labels, however, there is no active monitoring or prevention of unauthorized data sharing or loss.
Recommended approach:
- Identify and classify the sensitive data
- Use data encryption
- Secure your systems
- Implement DLP in phases.
- Implement a patch management strategy
- Allocate roles
- Automate
- Use anomaly detection
- Educate stakeholders
- Establish metrics
- Integrate Microsoft's DLP Data Labels or other third-party solutions
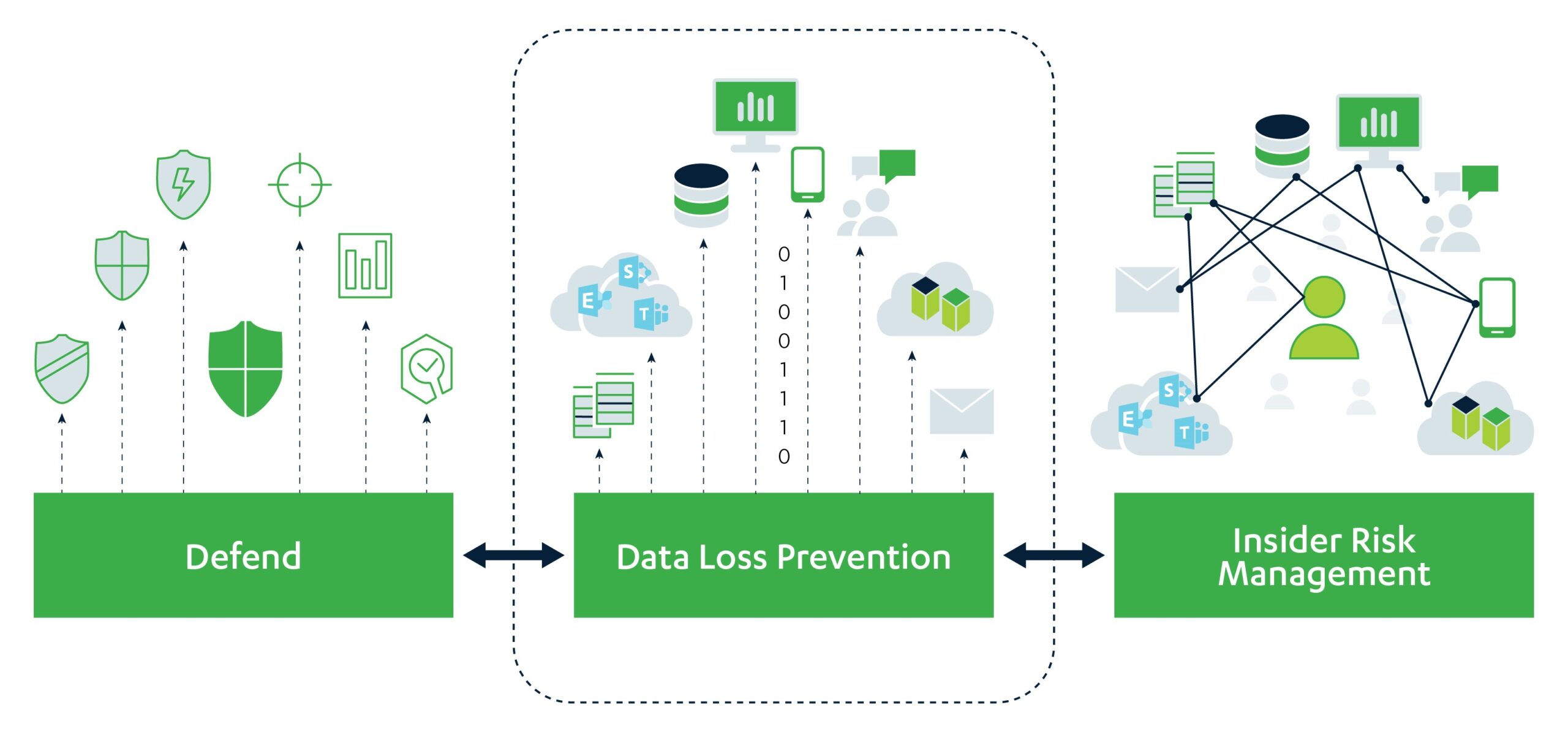
High-level Overview of DLP Data Labeling:
- Data Discovery: Identify and locate sensitive data within an organization's data repositories, databases, file servers, cloud storage, and third-party data sources, including dark data.
- Data Classification: Classify the sensitive data based on predefined categories or policies. This can include personally identifiable information (PII), financial data, health records, banking, tax, intellectual property, or client-specific data types.
- Labeling and Tagging: Apply labels or tags to the classified data to specify the sensitivity, associated policies, or restrictions. These labels assist in tracking, managing, and enforcing data protection measures through the Data Management lifecycle.
- Data Protection Policies: Define and implement data protection policies and DLP rules based on the labeled data. This includes specifying who can access, modify, or share the data and under what conditions.
- Monitoring and Enforcement: Employ DLP tools and services to monitor data usage and transmission both internally and externally, and proactively detect potential violations of the DLP policies. Analyze data in transit and at rest, including the scanning of emails, content storage, attachments, and the monitoring of user activities.
- Incident Response: Establish procedures to execute response mechanisms for potential data breaches or policy violations. Alert generation, stakeholder notification, incident analysis, and containment actions to mitigate risks, data loss, and exposure.
- Training and Awareness: Workforce education on data protection policies and procedures that promote a culture of security and privacy within a corporation. Reduce the likelihood of accidental data exfiltration or unauthorized access.
- Continuous Improvement: Constant process reviews modernize existing data label controls. Identify, categorize, and leverage automated or AI-driven protection policies to meet revised regulatory requirements for new and emerging threats. Increased risks are based on an organization’s exploding device estate, user types, and data landscape.

Subscribe to our newsletter for the latest updates.