Author: Angad Soni
Chief Architect, Business Applications & Data Modernization
Long View
Microsoft 365 Copilot is a powerful tool that leverages AI to enhance productivity. However, like any tool, it’s essential to ensure it is secure. This blog post will guide you through the best security setup for Microsoft 365 Copilot and the hierarchy of a security model.
Understanding the Components
Before we delve into the security setup, let’s understand the key components involved:
- SharePoint: It allows administrators to manage sites, designate site admins, manage sharing settings, and manage Microsoft 365 groups.
- OneDrive: It safeguards your data in the cloud and provides features like two-factor verification and encryption on mobile devices.
- Azure: It ensures the confidentiality, integrity, and availability of customer data.
- Groups: They allow admins to manage access to resources like SharePoint sites by grouping together users that require identical permissions.
- Sensitivity Labels: They let you classify and protect your organization’s data.
Best Security Setup
Here are some steps to ensure the best security setup for Microsoft 365 Copilot:
- Enable Two-Factor Authentication: This adds an extra layer of security by requiring users to provide two forms of identification before accessing their account.
- Use Sensitivity Labels: Apply sensitivity labels to documents and emails to classify and protect your organization’s data.
- Manage Access with Groups: Use Microsoft 365 security groups to manage access to resources efficiently.
- Leverage SharePoint and OneDrive Security Features: Use SharePoint groups and permission levels to manage access to sites. Also, leverage OneDrive’s features like two-factor verification and encryption on mobile devices.
Hierarchy of a Security Model
The hierarchy of a security model in Microsoft 365 Copilot should be as follows:
- Azure Active Directory (AAD): It is at the top of the hierarchy as it manages identities and access.
- Groups: They come next as they manage access to resources.
- SharePoint & OneDrive: They are responsible for managing sites and safeguarding data in the cloud.
- Sensitivity Labels: They are at the base of the hierarchy, providing a final layer of protection by classifying and protecting data.
In conclusion, securing Microsoft 365 Copilot involves understanding its components, implementing a robust security setup, and following a clear hierarchy in the security model.
Implementing Data Loss Prevention (DLP) Policy
In addition to these roles, you would also need to implement a Data Loss Prevention (DLP) policy:
- Identify Stakeholders: Identify the key individuals in your organization who will be responsible for implementing and managing the DLP policy.
- Describe the Categories of Sensitive Information to Protect: Determine what types of sensitive information your organization needs to protect. This could include financial data, health records, social security numbers, etc.
- Set Goals and Strategy: Define what you hope to achieve with your DLP policy and develop a strategy for how you will implement it.
- Design a DLP Policy: Create a policy intent statement and map it to a specific policy configuration.
- Create and Deploy Data Loss Prevention Policies: Map common policy intent scenarios to configuration options and configure those options.
- Investigate Data Loss Prevention Alerts: Understand the lifecycle of alerts from creation, through final remediation and policy tuning.
Remember, DLP policies are not just simple text scans. They use deep content analysis, evaluation of regular expressions, internal function validation, machine learning algorithms, and other methods to detect content that matches your DLP policies. This makes them an essential part of any robust security model.
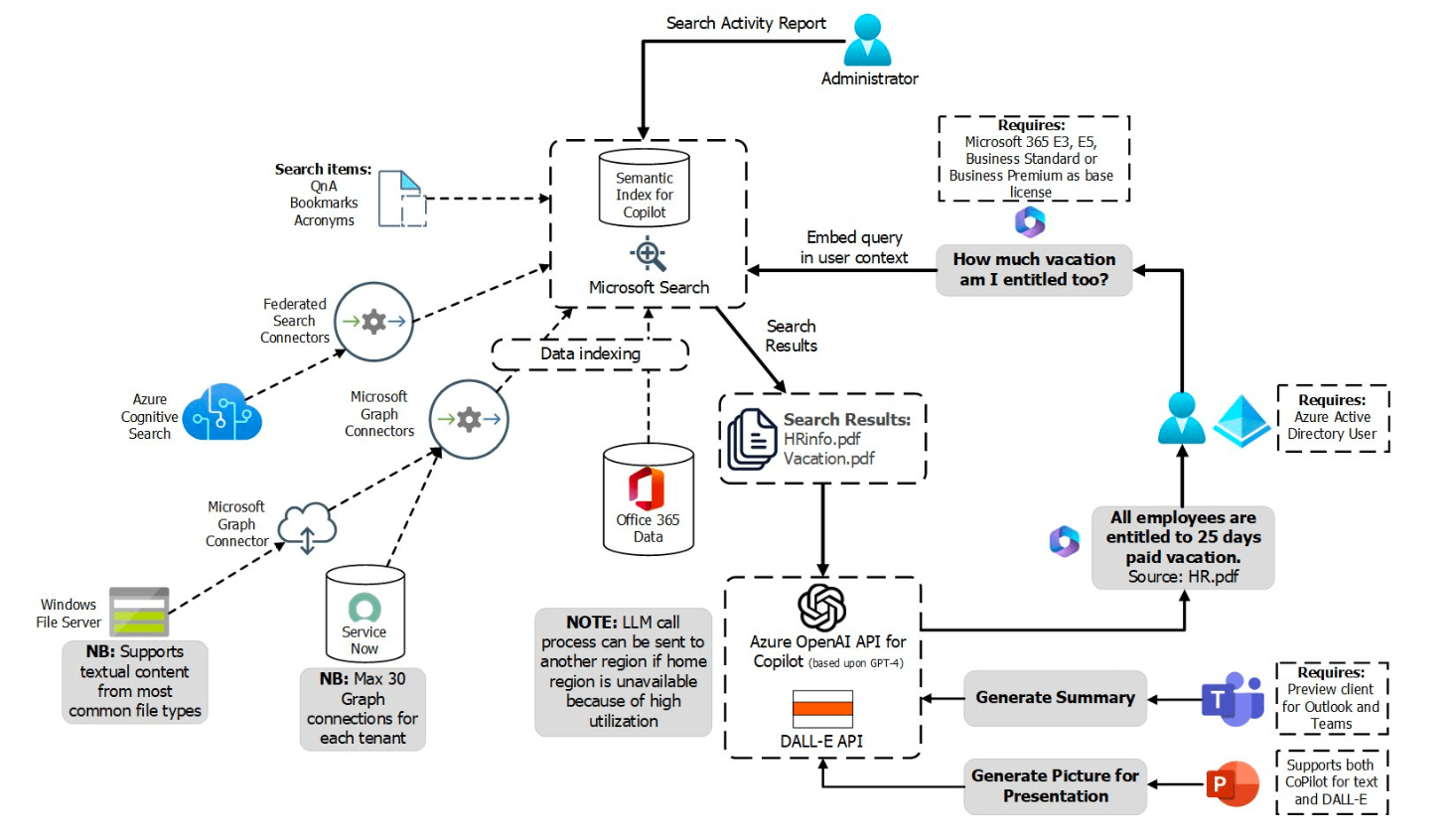
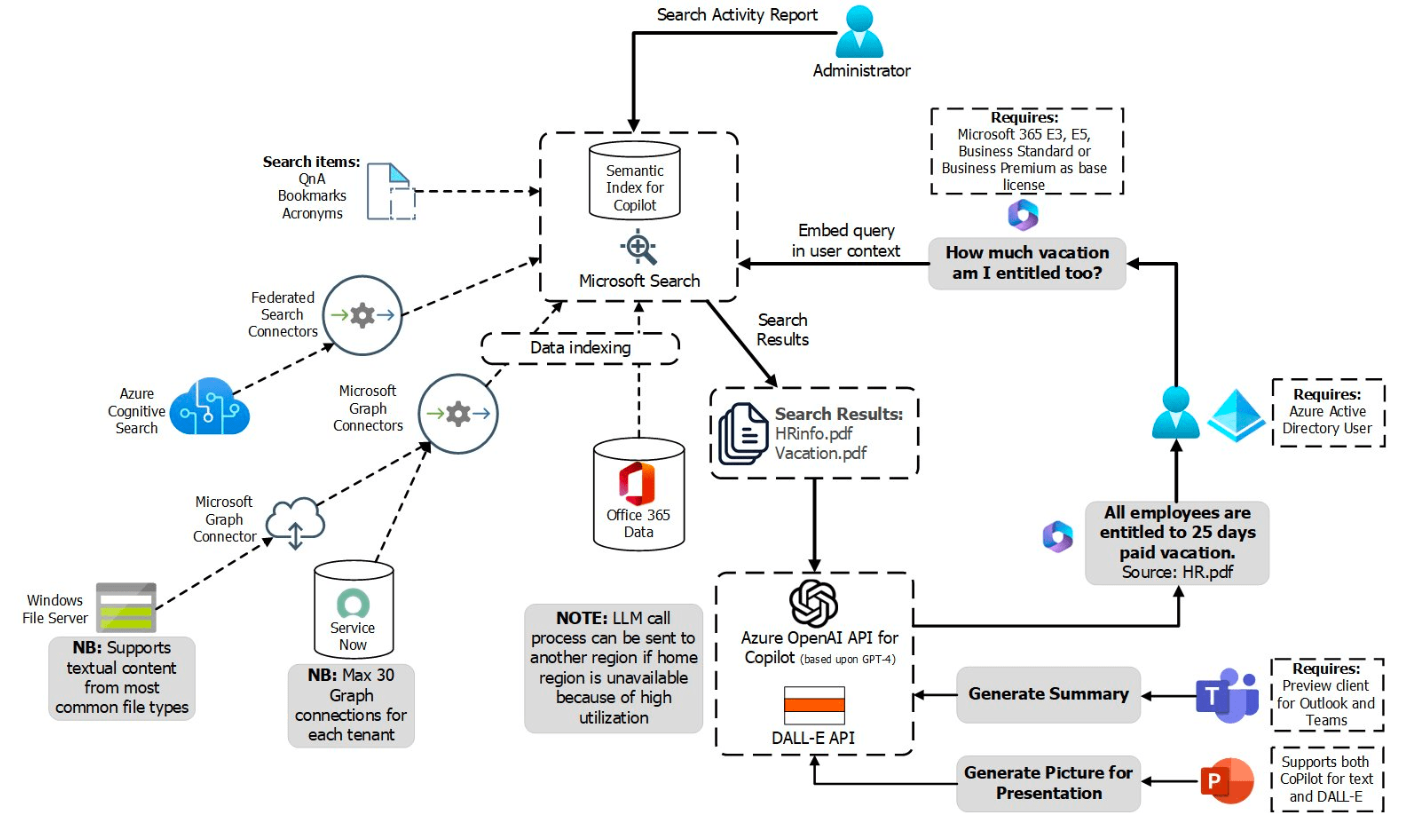
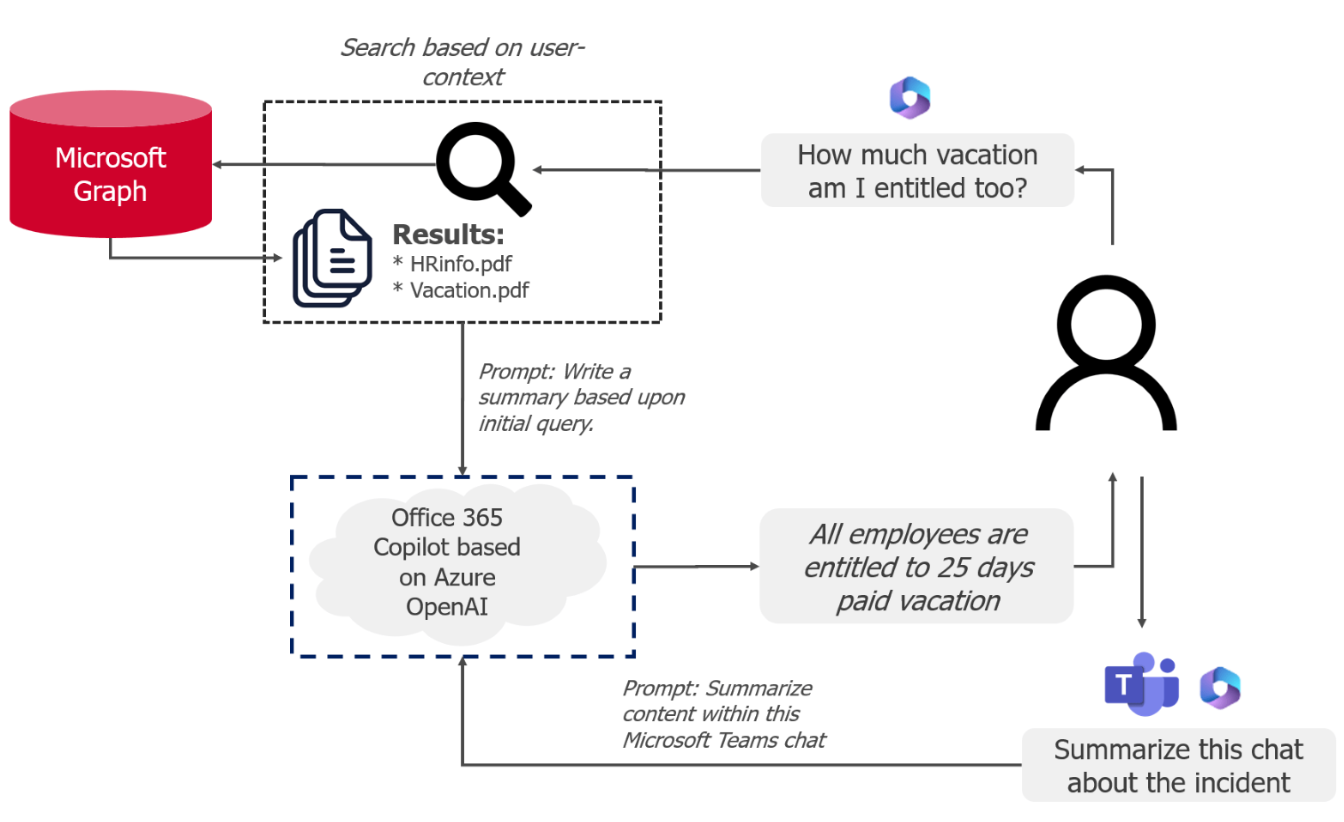
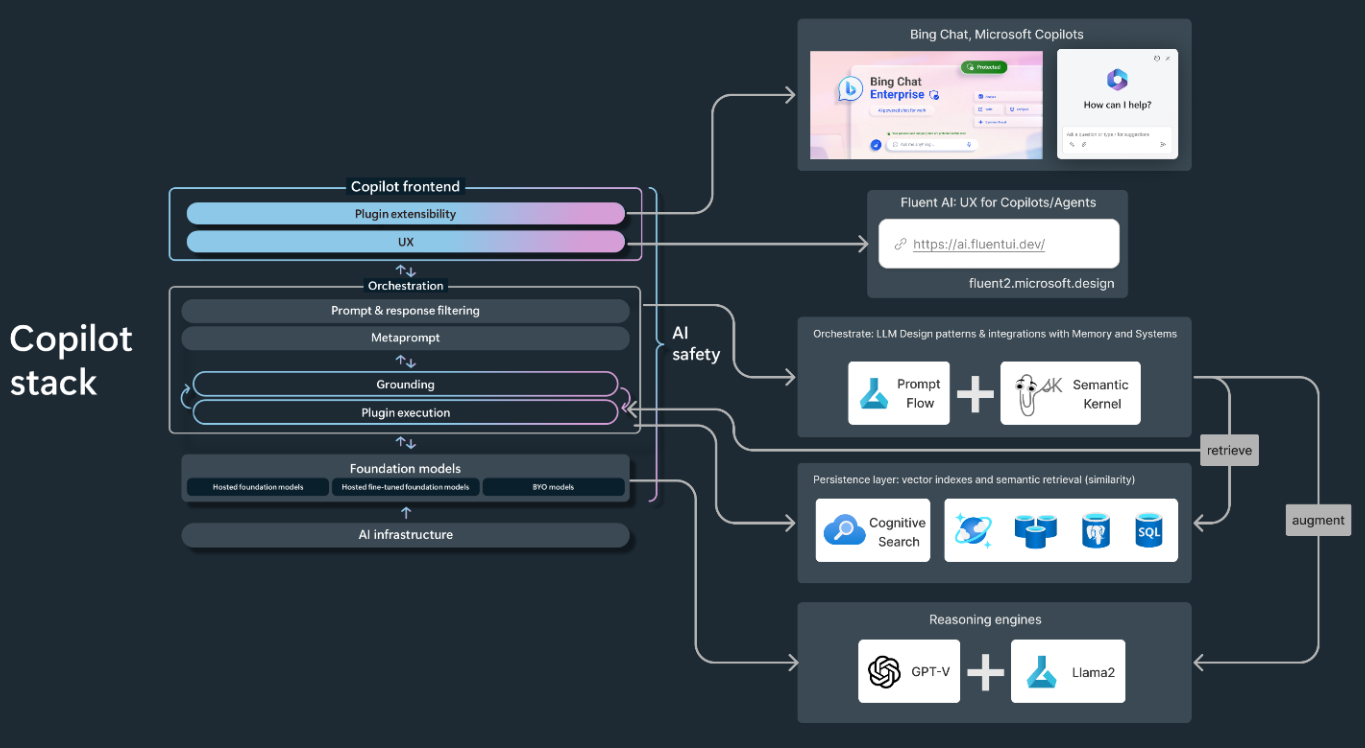
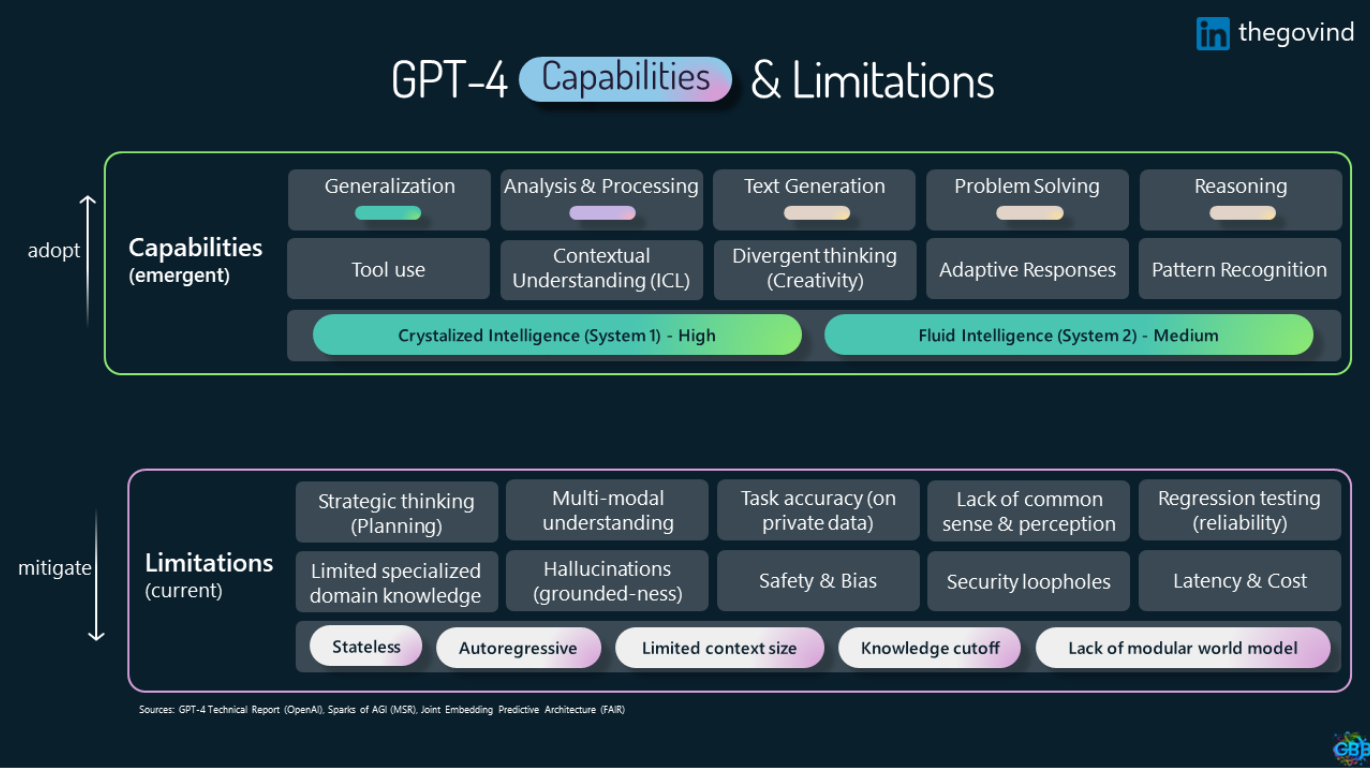
AI is transforming the way we work through tools like Copilot, but just like any tool, security is essential. Connect with our team to learn more about safely and securely integrating AI into your daily operations.
Suzanne Park

Subscribe to our newsletter for the latest updates.